Careers in Cybersecurity: Transitioning in 2025

Stay Informed With Our Weekly Newsletter
Receive crucial updates on the ever-evolving landscape of technology and innovation.
If you’re a professional contemplating a shift to cybersecurity, this field offers exciting prospects regardless of your previous experience. With competitive salaries, job security, and abundant opportunities, cybersecurity is a promising path to consider. As the industry grows, now is an ideal time to embark on this journey.
The ultimate goal of a cybersecurity career is to understand and mitigate cyber threats to protect organizations.
Why Now is the Right Time for Cybersecurity
Interested in a cybersecurity career? Visit the Institute of Data’s Cybersecurity Program page to download a course outline for free. Alternatively, contact our local team for a free consultation to discuss the program directly.
The demand for cybersecurity experts is soaring. With the increase in cyber threats and more businesses going digital, there’s a pressing need for professionals to safeguard data and systems by addressing system vulnerabilities. Governments and organizations globally are investing significantly in cybersecurity, making it a prime time to enter this field.
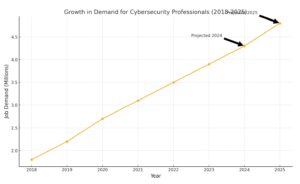
Cybersecurity Talent Crunch
The cybersecurity talent crunch is a pressing issue that the industry faces today. With the rapid increase in cyber attacks and the growing complexity of digital threats, the demand for skilled cybersecurity professionals has never been higher. By the end of the year, the industry is expected to have 3.5 million unfulfilled positions, highlighting a significant shortage of talent. According to a global survey by the Enterprise Service Group (ESG), 51% of IT decision-makers reported struggling to fill open positions. This shortage is further underscored by the World Economic Forum (WEF), which has identified cyber-attacks as the fourth most serious global concern, with data breaches ranking fifth. This critical gap in the workforce underscores the urgent need for skilled professionals to protect organizations from cyber threats and ensure the security of sensitive data.
Benefits of Cybersecurity for Career Changers
If you’re ready to pivot, take the first step by exploring our Cybersecurity Program. Learn more by downloading the course outline or scheduling a free consultation with one of our advisors.
Cybersecurity offers career changers an entry into a lucrative and sought-after field. It provides job stability, as organizations of all sizes need protection from cyber threats. Moreover, the variety of roles ensures there’s likely a position that aligns with your existing skills, even if your background isn’t technical.
Understanding the Cybersecurity Landscape
Key Industry Drivers
The key drivers for growth in the cybersecurity industry include increased online presence of businesses, rising cybercrime, stricter data protection regulations, and rapid digital transformation across all sectors. These factors are creating a need for skilled professionals who can manage security risks and protect against attacks.
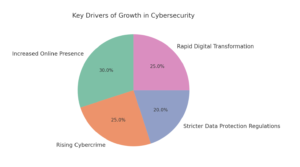
Source: Data influenced by industry reports on digital transformation, stricter data regulations, and rising cybercrime, such as insights from Gartner and the World Economic Forum.
Non-Tech Skills That Fit Well
Many skills from non-tech fields are highly valued in cybersecurity. For example:
- Risk Management: Understanding how to assess and mitigate risks is crucial.
- Project Management: Planning and executing security measures requires strong organizational skills.
- Communication: Clearly explaining security risks and procedures is essential in a team environment.
These skills can make your transition smoother and set you apart from purely technical candidates.
Where the Industry is Heading in Cyber Defense
The cybersecurity industry is rapidly evolving, with a focus on automation, AI-driven threat detection, and proactive risk management. Future trends include the growing importance of cloud security, the use of machine learning to predict attacks, and an increased focus on privacy and data security regulations.
Cybersecurity is booming, and there’s a big demand for people with skills in cyber defense and incident response. There are lots of different jobs, like security engineers, malware analysts, and ethical hackers. Each job role, such as penetration testers and blue teamers, plays a crucial part in maintaining and enhancing security measures within organizations by focusing on specific responsibilities and functions. You don’t need a tech background to get in—many non-tech skills are also really useful here.
Exploring In-Demand Roles for Security Engineers in Cybersecurity
| Role | Description | Responsibilities | Skills Needed |
| IT Support Technician | Provides foundational IT experience that is transferable to security roles | Troubleshooting IT infrastructure, supporting users, managing hardware/software issues | Knowledge of IT infrastructure, troubleshooting skills, customer service |
| Junior Security Analyst | Focuses on monitoring systems and analyzing threats | Monitoring alerts, analyzing security logs, assisting in incident response | Basic understanding of security tools and monitoring practices, analytical skills |
| GRC (Governance, Risk, and Compliance) Analyst | Ideal for those with experience in policy or auditing | Ensuring compliance with regulatory standards, creating policies, assessing risk | Knowledge of regulatory standards, policy development, risk assessment |
| Digital Forensics Analyst | Investigates digital media to uncover the truth behind digital incidents | Collecting and analyzing digital evidence, conducting investigations, creating reports | Skills in digital evidence collection, forensic analysis tools, attention to detail |
| Intrusion Analyst | Monitors systems for potential breaches | Monitoring network traffic, identifying suspicious activity, escalating incidents | Strong knowledge of network protocols and intrusion detection tools, analytical mindset |
| Incident Responder | Handles security incidents when they occur | Responding to and mitigating security breaches, conducting root cause analysis, implementing improvements | Ability to stay calm under pressure, strong problem-solving skills, understanding of incident response processes |
| SOC Analyst | Monitors an organization’s IT infrastructure for security threats | Reviewing logs, analyzing alerts, coordinating responses to security incidents | Knowledge of SIEM tools, strong analytical skills, understanding of attack vectors |
| Malware Analyst | Studies malware to understand and mitigate threats | Analyzing malicious software, developing defense strategies, reverse engineering code | Deep understanding of software, programming, reverse engineering, malware analysis tools |
| Penetration Tester | Simulates attacks to identify vulnerabilities in systems | Conducting security assessments, exploiting vulnerabilities, reporting findings | Strong knowledge of network and application security, familiarity with ethical hacking tools, problem-solving skills |
| Security Architect | Designs and oversees the implementation of secure network systems | Creating security frameworks, ensuring system integrity, guiding teams on best practices | Experience in security engineering, deep understanding of security protocols, strong strategic planning abilities |
| GRC Manager | Manages governance, risk, and compliance across an organization | Overseeing compliance programs, managing risk assessments, aligning security initiatives with business objectives | Strong understanding of regulatory requirements, leadership skills, strategic thinking |
| Chief Information Security Officer (CISO) | Leads the cybersecurity strategy of an organization | Developing security policies, overseeing the cybersecurity team, aligning security goals with business objectives | Leadership, strategic vision, extensive experience in cybersecurity management |
Each job role in cybersecurity, from penetration testers to blue teamers, plays a crucial part in maintaining and enhancing security measures within organizations.
Specialized Roles in Cybersecurity
Cybersecurity is a multifaceted field with a variety of specialized roles, each requiring unique skills and expertise. Here are some of the key roles you might consider:
- Threat Hunters: These professionals are on the front lines, using new threat intelligence to identify attackers who have evaded real-time detection mechanisms. Their proactive approach helps in uncovering hidden threats and mitigating potential risks.
- Red Teamers: Red Teamers adopt the mindset of an adversary, rigorously testing and measuring an organization’s detection and response capabilities. By simulating attacks, they help organizations strengthen their defenses and improve their security posture.
- Digital Forensics Analysts: These analysts delve into compromised systems and digital media to uncover the truth behind cyber incidents. Their work involves collecting and analyzing digital evidence to determine what happened and how to prevent future breaches.
- Malware Analysts: Facing attackers head-on, malware analysts dissect malicious software to understand its behavior and develop strategies to counteract it. Their expertise ensures a swift and effective response to cyber-attacks.
- Penetration Testers: Also known as ethical hackers, penetration testers simulate attacks on technology products to identify security loopholes. By exploiting vulnerabilities, they help organizations understand their risks and improve their defenses.
Each of these roles plays a crucial part in the broader cybersecurity landscape, offering diverse opportunities for professionals with different interests and skills.
How to Choose the Right Role for You
Choosing the right role depends on your interests and background. If you like solving puzzles, you might enjoy being a malware analyst. If you thrive under pressure, incident response might be a good fit. Research each role, consider your skills, and start with entry-level certifications to help narrow down your choices.
Some of the most in-demand roles are intrusion analysts, incident responders, and malware analysts. These jobs need certain cybersecurity skills, but you can transfer a lot of what you already know if you come from a different field. Plus, the pay is very competitive, which is a big plus for anyone making a career change.
Cybersecurity in Specific Domains
Cybersecurity is a critical concern across various industries, each with its unique challenges and requirements:
- Healthcare: In the healthcare industry, cybersecurity is vital for protecting medical devices and patient data from cyber-attacks. The sensitive nature of health information makes it a prime target for hackers, necessitating robust security measures.
- Finance: The finance industry is constantly under threat from cyber-attacks aimed at stealing sensitive financial information. Protecting customer data and ensuring the integrity of financial transactions are top priorities for cybersecurity professionals in this sector.
- Government: Government agencies handle vast amounts of sensitive information and are responsible for protecting critical infrastructure. Cybersecurity in this domain involves safeguarding national security and ensuring the resilience of essential services.
- Infrastructure: The Infrastructure Security Agency (ISA) plays a pivotal role in protecting the nation’s critical infrastructure from cyber threats. This includes everything from power grids to transportation systems, where a breach could have far-reaching consequences.
Each of these domains requires specialized cybersecurity strategies to address their unique vulnerabilities and protect against cyber threats.
Infrastructure Security Agency (ISA)
The Infrastructure Security Agency (ISA) is at the forefront of the nation’s efforts to enhance the security and resilience of its cyber ecosystem. The ISA’s mission includes protecting the federal “.gov” domain of civilian government networks and collaborating with the private sector to bolster the security of critical networks. The agency offers a range of job opportunities for cybersecurity professionals, particularly those with expertise in incident response and security. By working with the ISA, you can play a crucial role in safeguarding the nation’s critical infrastructure and ensuring the security of essential services.
Steps to Transition into a Cybersecurity Career
Assess Your Current Skills
Take stock of the skills you already have that could be useful in cybersecurity. Skills like risk management, problem-solving, and communication are all relevant. Knowing what you bring to the table can help you determine where to focus your learning efforts.
Finding the Right Career Path
Certifications are an important step in your cybersecurity journey. If you’re interested in knowing more about which certification is right for you, download our Cybersecurity Program outline or reach out for a free consultation.
Implementing Security Controls
Implementing security controls is a fundamental aspect of protecting organizations from cyber threats. These controls can be categorized into several types:
- Network Security Controls: Tools like firewalls and intrusion detection systems help monitor and protect network traffic, preventing unauthorized access and detecting suspicious activities.
- Data Security Controls: Measures such as encryption and access controls ensure that sensitive data is protected from unauthorized access and breaches.
- System Security Controls: Practices like patch management and vulnerability scanning help maintain the integrity of systems by identifying and addressing potential weaknesses.
- Incident Response Controls: Having a well-defined incident response plan and playbooks is crucial for effectively managing and mitigating security incidents.
Security engineers play a vital role in designing and implementing these controls, using threat intelligence to inform their decisions. Incident responders are equally important, as they use their knowledge of security controls to contain and remediate security issues. Together, these professionals ensure that organizations are well-equipped to defend against cyber threats and respond effectively to incidents.
Real-Life Success Stories
Successful Career Transitions
Are you inspired by these stories? Take the next step toward your own success by visiting the Institute of Data’s Cybersecurity Program page and learning how you can start your journey today.
Hearing from individuals who have successfully transitioned to cybersecurity can be both inspiring and motivating. These stories demonstrate that with determination, the right resources, and a willingness to learn, you too can achieve your goal of breaking into this dynamic field. The ultimate goal of these career transitions is to achieve proficiency in cybersecurity and contribute to organizational security. Here are two examples of people who made the leap and found success in cybersecurity.
From Travel to Cybersecurity: Ez’s Journey to a New Career
Ez Yiap’s story is a testament to resilience and adaptability. With a background in the travel industry, Ez faced an uncertain future when the global travel sector came to a halt. Determined to pivot, Ez enrolled in a Cybersecurity Program with the support of a generous AIR Scholarship designed to help displaced travel industry professionals transition into tech roles.
Key Elements of Ez’s Success:
- Mentorship and Training: Ez was guided by experienced cybersecurity professionals who provided industry insights and hands-on training.
- Accelerated Learning: Within just six months, Ez gained the knowledge and skills necessary to secure a role in cybersecurity.
- Exploring Opportunities: As Ez put it:
“There’s such an incredible opportunity to learn, grow, and move within the cyber industry. From roles that are super technical to people-focused, and everything in between.”
Outcome: Ez successfully landed a cybersecurity role even before completing the 24-week part-time course. Today, Ez sees a world of possibilities in the cybersecurity field, a stark contrast to the limited prospects in the travel industry.
From Kitchen Hand to Cybersecurity Analyst: Matt’s Transformation
Matt’s story illustrates how determination and practical skills can completely transform a career. In 2020, Matt worked in the hospitality industry as a kitchen hand. While he valued the interpersonal skills he developed in hospitality, he was eager to pursue a career with more growth potential and stability.
Steps Matt Took to Transition:
- Focused Skill Development: Matt concentrated on building practical cybersecurity skills, including hands-on training and simulations.
- Guidance from Experts: Like Ez, Matt benefited from mentorship provided by seasoned professionals in the industry.
- Applying Transferable Skills: His interpersonal skills, such as communication and teamwork, helped him stand out in a new context.
Outcome: Matt secured a role as a Cybersecurity Analyst before completing his training. Reflecting on the transition, he shared:
“My career outlook has been completely turned around. I’m enjoying what I do now more than ever and am excited to keep progressing.”
Lessons Learned from Ez and Matt
- Mentorship Matters: Both Ez and Matt emphasized the importance of guidance from industry experts, which helped them navigate the challenges of entering a new field.
- Transferable Skills are Valuable: Skills like communication, teamwork, and adaptability played a crucial role in their success, even in a technical field like cybersecurity.
- Accelerated Learning Works: With focused programs and real-world training, they were able to transition quickly, proving that a career change to cybersecurity doesn’t have to take years.
These success stories highlight the potential for anyone, regardless of their starting point, to thrive in cybersecurity. With the right mindset, training, and support, you can make a similar leap into a rewarding and future-proof career.
Challenges Faced by Career Changers
Career changers often face challenges such as adapting to new technology and gaining experience. The good news is that these challenges can be overcome with structured learning and persistence. Many successful professionals in cybersecurity have made the leap from non-tech fields by dedicating time to learn and practice.
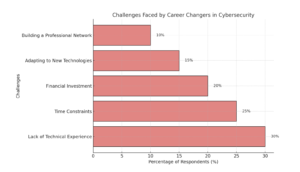
Source: Challenges based on feedback and insights from career transition studies, such as the ISC² Workforce Study and Indeed Career Guides.
Overcoming Barriers in Cybersecurity Incident Response
Barriers like lacking technical experience can be addressed by starting small. Use beginner-friendly resources, join communities, and seek mentorship. Real-life stories show that perseverance and hands-on practice can turn these barriers into stepping stones for success.
Lessons Learned from Successful Transitions
Those who have transitioned into cybersecurity often emphasize the importance of patience, continuous learning, and networking. They also suggest starting with entry-level roles to build a solid foundation before advancing. These lessons can guide you in your own career journey.
Lots of people have switched to cybersecurity from non-tech fields and have done really well. They faced challenges, but used their strengths to find success. Their stories can offer good advice and encouragement for anyone looking to do the same.
The Benefits of a Career in Cybersecurity
Job Stability and Security
Cybersecurity offers excellent job stability due to the high demand for experts. Every business needs protection from cyber threats, ensuring a steady flow of opportunities. Unlike many other industries, cybersecurity jobs are less likely to be outsourced or automated, providing peace of mind for job seekers.
Career Growth Opportunities
There are numerous growth paths in cybersecurity. You can start as an incident responder and work your way up to become a security architect or even a CISO. The field also offers the chance to specialize in areas like threat intelligence, ethical hacking, or digital forensics, providing plenty of options for career advancement.
Making an Impact
Working in cybersecurity allows you to protect people and organizations from real-world threats. By preventing cyber attacks, you help secure sensitive data, maintain privacy, and keep critical infrastructure running. It’s a career where you can make a tangible difference every day.
Cybersecurity jobs are stable, and there’s a growing demand for them. There are lots of opportunities to grow, from starting-level jobs to leadership positions like CISO. These jobs are also fulfilling, as you get to protect important data and prevent cyber attacks.
Practical Tips for Getting Started
Ways to Gain Experience
Gaining experience is key to breaking into cybersecurity. If you’re unsure where to start, our Cybersecurity Program offers hands-on labs and training to help you gain real-world skills. Reach out today for more information.
Gaining experience is key to breaking into cybersecurity. Here are some options:
- Internships: Many companies offer cybersecurity internships.
- Freelance Projects: Work on small security projects for individuals or businesses.
- Open-Source Contributions: Help with open-source security tools or projects.
Any hands-on experience can significantly boost your resume and skills.
Networking Strategies for Cybersecurity
Networking is crucial for career growth. Here are some strategies:
- Join Cybersecurity Groups: Find online forums or local meetups.
- Attend Industry Events: Conferences and webinars are great places to meet people.
- LinkedIn Connections: Reach out to professionals and engage with their content.
Building a network can help you find job leads, mentors, and valuable insights.
Preparing for Your First Job Interview
To prepare for your first cybersecurity interview:
- Review Common Questions: Be ready to discuss technical concepts and problem-solving approaches.
- Showcase Projects: Talk about hands-on projects or labs you’ve completed.
- Highlight Transferable Skills: Emphasize skills from your previous roles that apply to security.
Good preparation can help you feel confident and make a strong impression.
To get experience, try internships, freelance work, or contributing to open-source projects. Join cybersecurity communities, attend events, and connect with others for support and mentorship. Make sure your resume highlights your skills and prepare well for interviews to help you get your first job.
Next Steps You Can Take Today
Ready to make a change? Visit the Institute of Data’s Cybersecurity Program page to download a course outline for free. If you’d like to discuss your career change in more detail, contact our local team for a free consultation.
Cybersecurity is a solid career choice for 2025, with lots of chances to grow, good job security, and meaningful work. Start today by setting some goals, like getting a certification or talking to someone in the industry to learn more.


